Okta Single Sign-On
Okta is a cloud-based identity and access management platform that supports
SAML 2.0, OpenID Connect, and OAuth 2.0. You can use Okta as a SAML 2.0 Identity Provider to bring
your Okta users into Uptrace.
Single Sign-On allows you to manage users using SAML providers. After logging in, such users are
automatically added to a team and can access team projects. When users are removed from Okta, they
automatically lose granted access in Uptrace.
Step 1. Create SAML SSO in Uptrace
- In Uptrace, go to Organization -> Single Sign-On
- Click New SSO -> New SAML
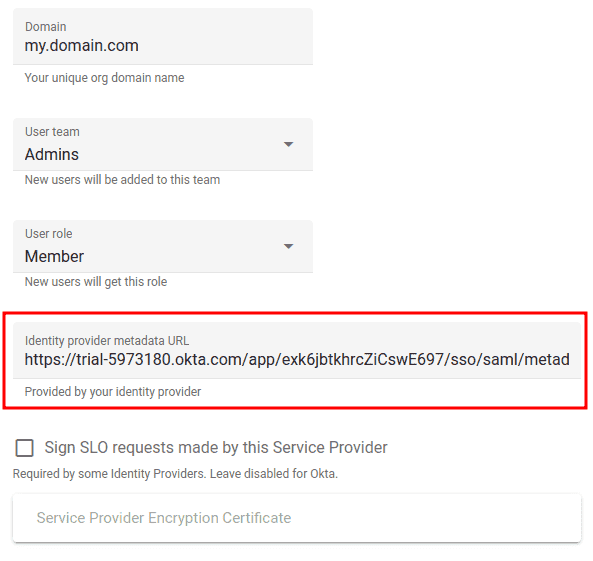
- Fill out the form:
- Domain: your unique domain name (can be any string; it will be used later during the sign-in
process) - User team: select the team that will be automatically assigned to new users
- User role: select the role that will be automatically assigned to new users
- Domain: your unique domain name (can be any string; it will be used later during the sign-in
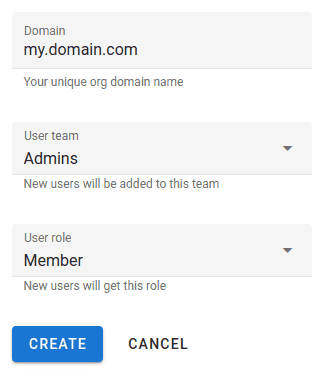
- Click Create and you will be presented with the service provider information required to
configure Okta
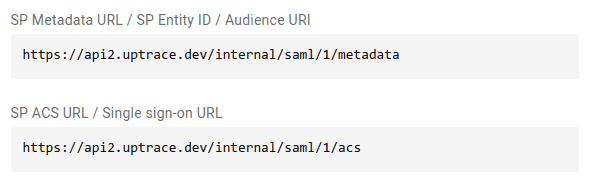
Leave this form open — you will need to enter the Metadata URL from Okta to finish the setup.
Step 2. Create an app integration in Okta
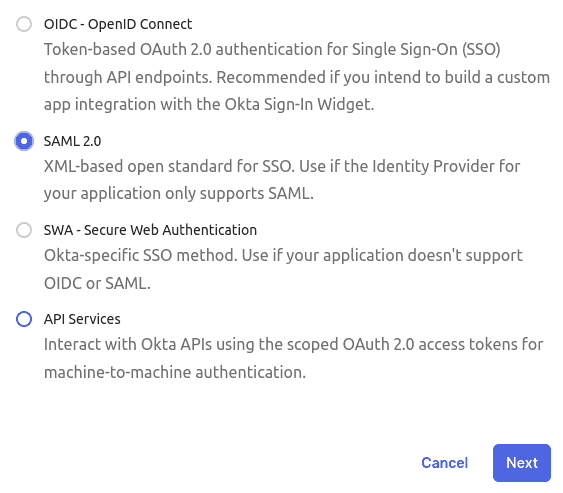
- In Okta, go to Applications and click Create App Integration
- In the dialog window, select SAML 2.0 and click Next
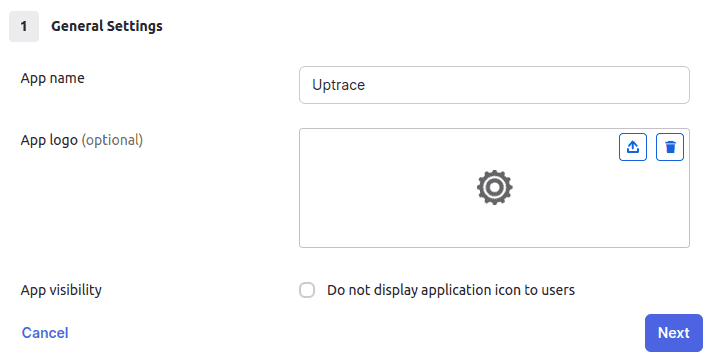
- In the General Settings tab, use
Uptraceas the app name and click Next
Step 3. Configure SAML settings
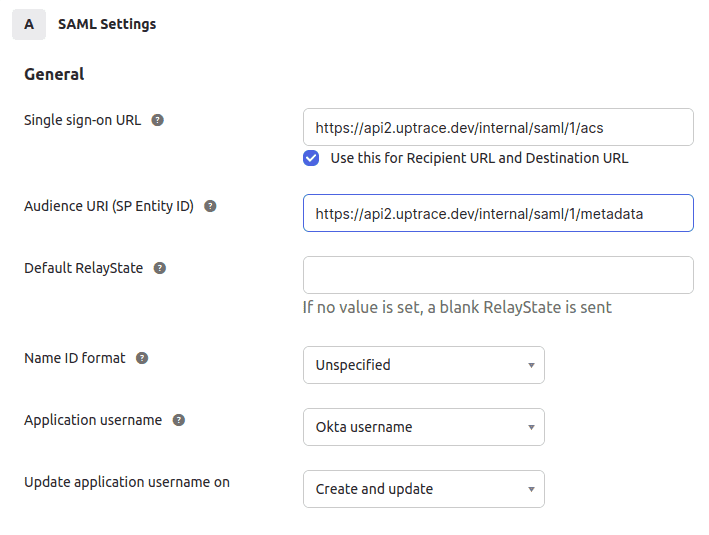
- In the Configure SAML tab, use the service provider information you received from Uptrace in
Step 1 to fill in the Single sign-on URL and Audience URI (SP Entity ID) fields
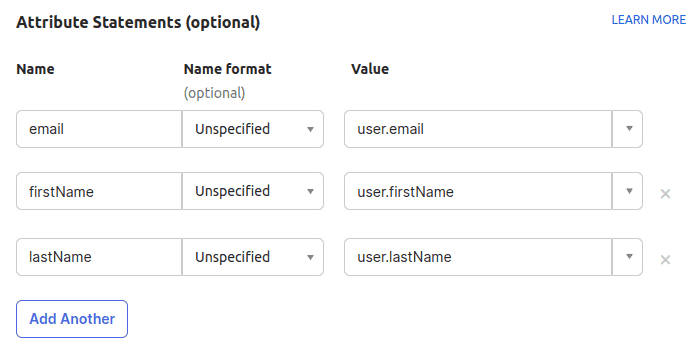
- On the same page, scroll down to Attribute Statements and add the following attributes:
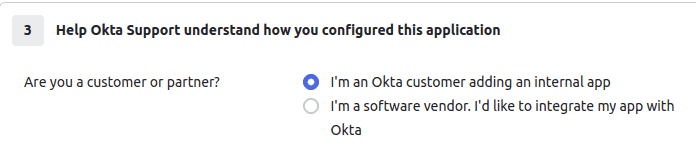
- Click Next to go to the feedback page. Select the appropriate option and click Finish
Step 4. Get metadata URL
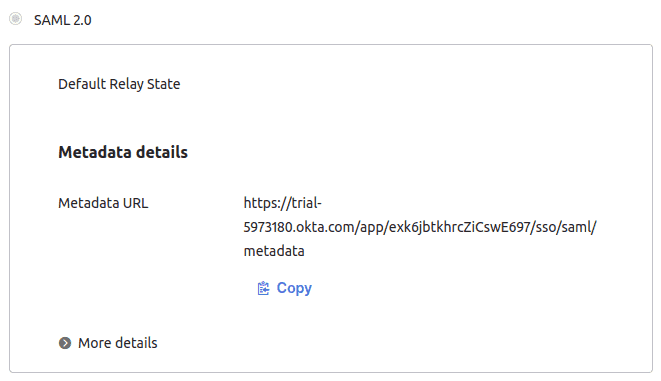
- You should land on the Sign On tab for your new application
- Find and copy the Metadata URL — you will need it to finish configuring Uptrace
Step 5. Finish configuring Uptrace
- Go back to the SAML SSO form you left open in Step 1
- Enter the Metadata URL you copied from Okta in Step 4
- Click Save
You can now log in to Uptrace using Okta by openinghttps://uptrace.dev/auth/sso/<your-domain>.
Troubleshooting
Metadata URL not accessible — Uptrace needs to fetch the metadata URL from Okta to obtain the
SAML certificate and endpoints. Make sure the URL is reachable from the Uptrace host.
Attribute statements missing — Uptrace requires email and name attributes from the SAML
assertion. Make sure you configured the attribute statements as described in Step 3.
User has no email — Uptrace requires an email address for SSO users. Make sure the Okta user has
an email configured in their profile.